Active Directory (JNDI)
Overview
The Active Directory Connector supports provisioning to Windows servers 2003 / 2008 running Active Directory.
In order to have all the functionalities available with Windows server 2003 you have to raise functional level and forest functional level.
Please take a look at raise forest function level for more details.
This bundle is fully implemented in Java and makes use of JNDI to communicate to Active Directory, hence it does not require any additional module.
Installation
To install the Active Directory connector, add the bundle JAR file to a directory on your disk. If your application has a dedicated directory for connector bundles, put the file in that directory. For example, Apache Syncope looks for connector bundles in the configured bundles directory.
Supported Operations
The Active Directory connector supports the following operations:
- Authentication
- Create
- Update
- Delete
- Get (read)
- Schema (ask for schema)
- Search
- Sync
- Test
- Validate
Configuration
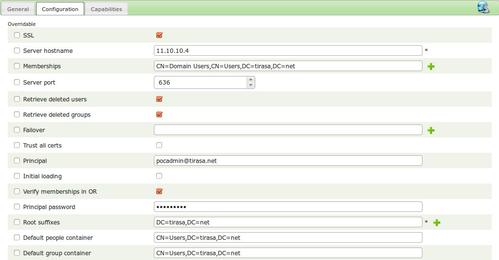
The following table lists all the configuration properties you can specify when setting up the Active Directory connector:
| Configuration Property | Required | Type | Default Value | Description |
|---|---|---|---|---|
| SSL | X | Boolean | true | Use SSL to perform password provisioning. Every operation can be performed by using a non-SSL connection: the only limitation is about user creation: active users cannot be created because password values cannot be provisioned. |
| Server hostname | X | String | Active Directory server on which to connect | |
| Server port | int | 636 | AD SSL port on which to connect. Plain connection is possible. See SSL property for known limitations. | |
| Failover | String array | An array of LDAP URLs specifying failover servers. If the connector cannot make a connection to the server specified in thehost property, it will try connecting to these failover servers in the specified order. | ||
| Principal | String | Distinguished name (DN) of the Active Directory entry under to perform provisioning operations | ||
| Principal password | GuardedString | Password corresponding to the entry specified in the principal property | ||
| Base contexts for user entry searches | X | String array | DN of context to be used as starting point for account searches. The connector ignores any entries outside these base contexts but the default people container. | |
| Base contexts for group entry searches | String array | DN of context to be used as starting point for group searches. The connector ignores any entries outside these base contexts but the default group container. | ||
| Default people container | String | Default people container to be used during create in case of entry DN is not explicitly provided. | ||
| Default group container | String | Default group container to be used during create in case of entry DN is not explicitly provided. | ||
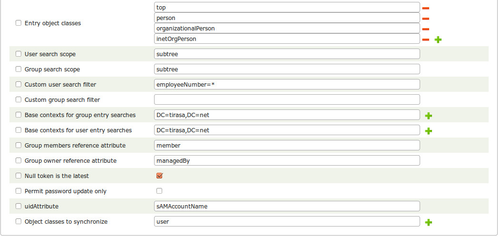
| Entry object classes | String array | { "top", "person", "organizationalPerson", "user" } | Object classes to which the ACCOUNT object class is mapped. | |
| Custom user search filter | String | LDAP search filter for accounts. When searching for accounts, the connector only considers those accounts that match the specified filter. | ||
| Custom group search filter | String | LDAP search filter for groups. When searching for groups, the connector only considers those groups that match the specified filter. | ||
| Root suffixes | X | String array | Base context DNs to use for synchronization. The connector ignores any changes outside of these base contexts. | |
| Object classes to synchronize | String array | "user" | User object classes to synchronize. The connector ignores any changes if it cannot find any of the modified entry's object classes in this property. | |
| Memberships | String | Groups to identify users to synchronize. The connector ignores any changes about users not member of indicated groups | ||
| Retrieve deleted users | Boolean | true | Indicate if deleted users must be synchronized also. | |
| Retrieve deleted groups | Boolean | true | Indicate if deleted groups must be synchronized also. | |
| Trust all certs | Boolean | false | Indicate if all server certificates must be trusted. | |
| Verify memberships in 'OR' | Boolean | false | Indicate if specified memberships must be verified using 'OR' logical operator. | |
| User search scope | String | subtree | Choose object, onlevel or subtree | |
| Group search scope | String | subtree | Choose object, onlevel or subtree | |
| Group members reference attribute | String | member | Group attribute referencing (by DN) the users members of a group | |
| Group owner reference attribute | String | managedBy | Group attribute name referencing (by DN) the owner | |
| Null token is the latest | Boolean | true | Reset null token value to the latest (sync with null token won't return any result). | |
| Permit password update only | Boolean | false | Permit password update only. Create/delete operation will be denied while other attributes update requests will be ignored. If checked and a password update is requested then user status (UAC value) won't be changed unless “User must change password at next logon” is set. In that case this flag is removed and the password is accepted as the default password. | |
| Conservative membership policy | Boolean | false | Conservative management of assigned groups. The groups already assigned to an user on AD will not be removed. | |
| Exclude attribute changes on update | Boolean | false | Exclude attribute changes on update. The only operations allowed will be the assignment and removal of groups. |
Main configuration notes
- Active Directory connector provides password provisioning using a secure connection only. ADs port must be always provided.
- Provided Memberships (a list of group DNs) will be used to compose the user (not group) search filter on memberOf attribute.
Each membership will be evaluated in or/and based on Verify memberships in 'OR'. - Provided Custom user search filter/Custom group search filter will be used to compose (in AND) the user/group search filter.
- Object classes to synchronize will be the first filter applied to retrieve users to be synchronized.
All the users matching this first filter will be filtered again with the second filter based on memberships, verify memberships in 'OR' and custom user search filter. - There are no specific parameter to specify group object classes to be synchronized.
All the groups (identified by the object classes top and group) to be synchronized will be filtered by custom group search filter (if provided). - Use retrieve deleted users to synchronize user deletions.
- Use retrieve deleted groups to synchronize group deletions.
- Check trust all certs to avoid server certificate validation (to be used if no CA certificate available or server certificate cannot be validated).
- Perform the first synchronization by performing a full search upfront. See the following suggested steps:
a. search users to be synchronized by the Search feature provided by the connector (providing your custom ldap filter if needed);
b. check Null token is the latest;
c. perform your synchronization (just needed to initialize the syncToken to the lates operation - no results will be returned);
e. schedule your future synchronizations ....
The following images show a sample configuration provided on Apache Syncope.
Advanced user management
- You can unlock user by performing an update sending lockoutTime boolean attribute to true.
- You can reset user password change mandatory constraint by performing an update sending pwdLastSet boolean attribute to true.
- You can set/unset user cannot change password condition by performing an update or create sending userCannotChangePassword boolean attribute to true/false respectively.
- You can set/unset "don't expire password" by performing an update or create sending passwordNeverExpires boolean attribute to true/false respectively (available from 1.2.7, 1.3.5).
- You can specify a primary group ID for an object by performing a create/update operation including the DN of the primary group to be specified into the set of provisioning attributes.
Use the special attribute primaryGroupDN to send this information.
Please note that this specific feature is available from 1.2.3 onwards.